Which Statement Best Describes Asymmetric Key Encryption
Engaging in the separation of duties. Asymmetric encryption is the strongest hashing algorithm which produces longer and more secure digests than symmetric encryption.
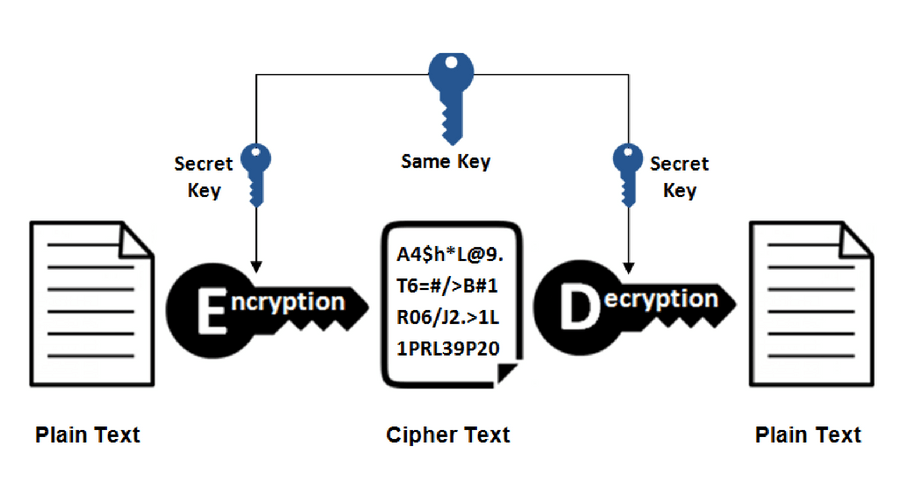
What Is Cryptography Cryptography Is Used To Secure And By Jeevithaa Beyondx Medium
In Symmetric-key encryption the message is encrypted by using a key and the same key is used to decrypt the message which makes it easy to use but less secure.

. Which statement best describes asymmetric-key encryption. The asymmetric encryption is often used for securely exchanging secret keys. A private key and a public key.
Asymmetric algorithms use two keys. A public key and a private key. Which statement best.
They have key lengths ranging from 80 to 256 bits. The same key is used for encryption as well as decryption. Two different cryptographic keys asymmetric keys called the public and the private keys are used for encryption and decryption.
The public key is known to all sending and receiving parties involved in. These are the tradeoffs worth considering when deciding which type of encryption to employ. An attackers attempt to decode a cipher by attempting each possible key combination to find the correct one How many encryption key bits are needed to double the number of possible key values that are available.
Asymmetric encryption requires substantially more overhead computing power than symmetric encryption. The opposite is also true. Asymmetric key encryption uses a single key for both encryption and decryption.
An encryption method in which a key is required to encrypt data for storage and verify its integrity. Which statement describes asymmetric encryption algorithms. Which statement best describes symmetric-key encryption.
Symmetric encryption is much faster to execute because of its shorter key lengths. An encryption method in which numbers generated by an algorithm from a text string are used to verify the integrity of transmitted messages. An encryption method in which two separate keys -- a private key and a public key -- are used to encrypt and decrypt a message Which statement best describes asymmetric-key encryption.
The reverse is also true. Asymmetric key encryption uses a single key for both encryption and decryption. Asymmetric key encryption uses three separate keys for both encryption and decryption.
It also requires a safe method to transfer the key from one party to another. Which of the following best describes an asymmetric key encryption strategy. An encryption method in which both private key and a public key -- are used to encrypt and decrypt a message Which of the following search engines was the first to determine a sites relevance based upon the number of links that point to it in addition to ranking its relevance according.
Asymmetric encryption has a tendency to bog down networks because of its longer key lengths and complex algorithms. They are relatively slow because they are based on difficult computational algorithms. Both keys are capable of the encryption process but the complementary matched key is required for decryption.
Asymmetric key encryption uses two private keys to encrypt and decrypt messages. Which of the following statements best describes asymmetric key encryption. Asymmetric key encryption uses both a private and public key to encrypt and decrypt messages.
Asymmetric Encryption is slow in execution due to the high computational burden. Asymmetric encryption is inefficient when transferring or encrypting large amounts of data. Birthday attack What best describes a brute-force attack.
If a public key encrypts the data the matching private key decrypts the data. Asymmetric key encryption uses both a private and public key to encrypt and decrypt messages. Data encrypted with the public key can only be decrypted using the private key.
Asymmetric encryption is an encryption model that requires two keys for example Key A and Key B. 1Which of the following statements best describes asymmetric key encryption. Symmetric Key vs Asymmetric key.
Usually these keys can be used interchangeably such that if you use Key A to encrypt data you can use Key B to decrypt this information and if you use Key B to. They are also called shared-secret key algorithms. The symmetric encryption is used for bulk data transmission.
Which statement best describes asymmetric-key encryption. Asymmetric key encryption uses public and private keys. Asymmetric key encryption uses two private keys to encrypt and decrypt messages.
Symmetric key encryption uses only one key both to encrypt and decrypt data. Asymmetric encryption also called asymmetric-key encryption or public-key encryption refers to an encryption method in which two keys are used to encrypt and decrypt a message. Which of the following statements best describes asymmetric key encryption.
The file is encrypted with a private key and can be decrypted with a public key. An encryption method in which a key is required to encrypt data for storage and to verify its integrity. A cryptographic security mechanism that uses public and private keys to encrypt and decrypt data.
Symmetric encryption is fast in execution. Computer Science questions and answers. Which of these statements about symmetric key encryption is true.
The key can be made publicly available. Symmetric Key Encryption. An encryption method in which numbers generated by an algorithm from a text string are used to verify the integrity of transmitted messages.
Symmetric key encryption is used for SSL. A cryptographic security mechanism that uses the same key for both encryption and decryption. Only one key symmetric key is used and the same key is used to encrypt and decrypt the message.
DES 3DES and AES are examples of symmetric. They include DES 3DES and AES. AA cryptographic security mechanism that uses two separate sets of public and private keys to encrypt and decrypt data bA cryptographic security mechanism that uses public and private keys to encrypt and decrypt.
Which statement best. Asymmetric Key Encryption is based on public and private key encryption technique. It works in such a way that the information that Key-A can encrypt while Key-B can decrypt.
DES 3DES AES and RC4.

Si110 Asymmetric Public Key Cryptography
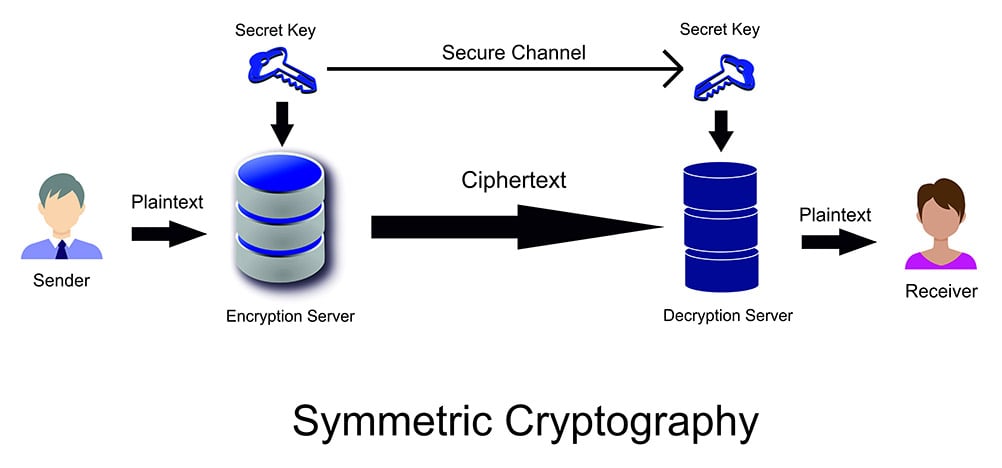
Symmetric Vs Asymmetric Encryption What S The Difference
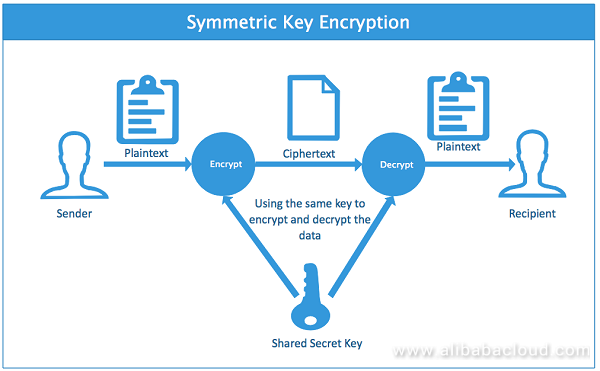
Sql Server Best Practices Using Asymmetric Keys To Implement Column Encryption By Alibaba Cloud Medium
Comments
Post a Comment